Welcome to the 11th episode,
We all recall the days when we used to write handwritten letters to our friends and relatives.Those envelopes are hand-sealed with tenderness and love.
We all browse every day and there is lot of data that travels over the internet and some times we even share sensitive information like credit card while we shop.
There are always bad guys out there, to intercept and steal that sensitive information. In order to protect information or make it unreadable to those trying to break-in, we need a process and that's exactly what encryption is for. Only the intended recipient will be able to read the information by decrypting it successfully.
Cryptography is the study of encrypting and decrypting information for secure transmission between two entities.
Encryption is the process of converting plain text into code, or ciphertext.
Decryption is the reverse - converting ciphertext back to plaintext.
Why is it important?
Businesses have three significant tools to help protect both user and internal data out of the hands of the wrong people.
Encryption, authentication, and authorization are three of them !
Symmetric Encryption:
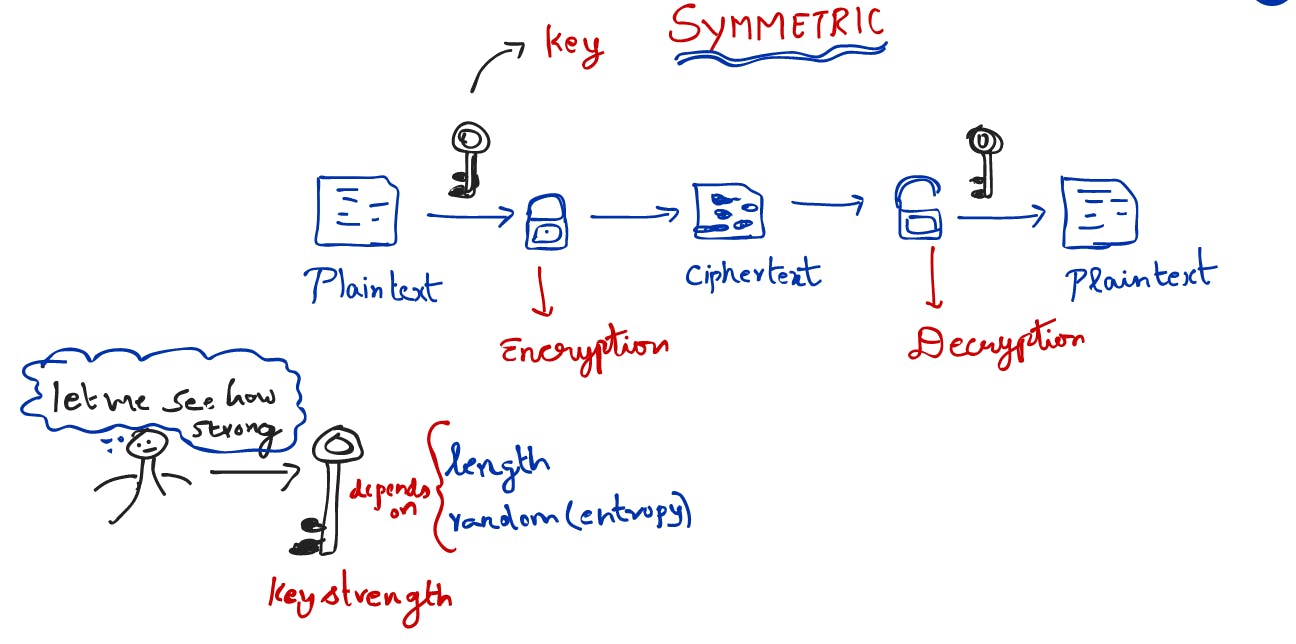
Symmetric encryption uses the same key for both encryption and decryption. It's fast and easy, provided that the key stays secret.
The key's strength depends on
1) The length of the key.
AES-256, which has a key length of 256 bits, supports the largest bit size and is practically unbreakable by brute force based on current computing power, making it the strongest encryption standard
Well, someday as computers and its computing powers evolve, just like how 128 bit and 192 bit encryption were succeeded by 256 bit, we may have to increase the length few years from now.
2) Its entropy (or, the "randomness" inherent in creating it)
I know you heard that, in you physics or thermodynamic class! Yes it represents the degree of disorder in a system. Similarly in cyptography we want to see this "randomness" every single time, making it harder for the bad guys.
Block or Stream
Block ciphers and stream ciphers are two separate methods of encrypting data with symmetric encryption algorithms:
Block ciphers encrypt data in blocks, where stream ciphers encrypt data one bit at a time. AES, or the Advanced Encryption Standard is a block cipher using a 256-bit key is considered unbreakable.
Good Reads: block-cipher-vs-stream-cipher
Asymmetric Encryption
This is just like running a crowd funding. Everyone gets a copy of your public key that they can use to put money in your account, but only you who own the private key can pull the money out.
Asymmetric encryption uses two different keys for encryption and decryption. The encryption (public) key is visible to all, while the decryption key stays private. Asymmetric encryption takes longer, but it's considered to be more secure.
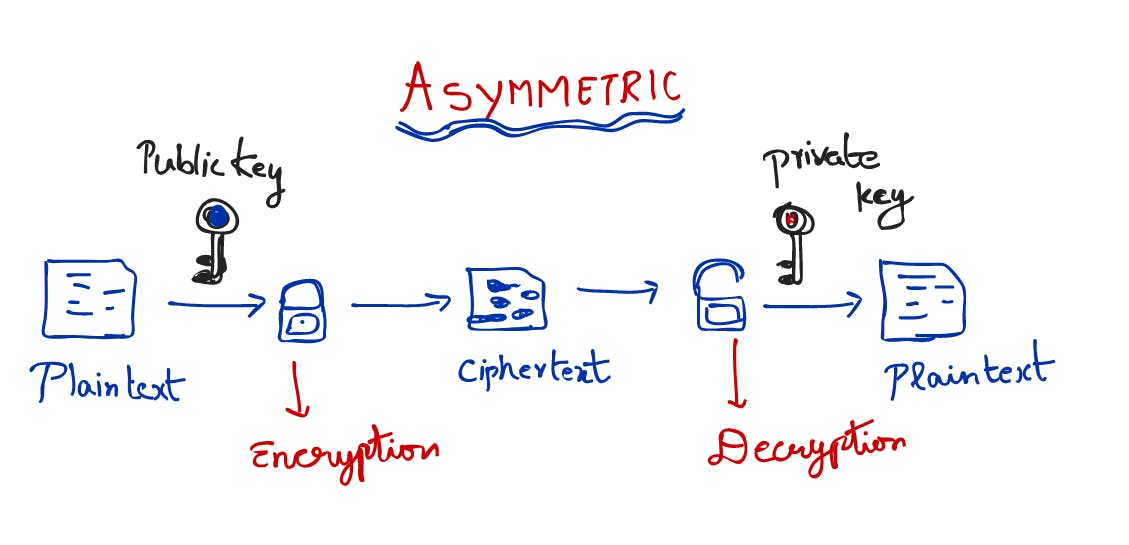
Some well-known examples of asymmetric encryption algorithms include RSA, which was developed alongside early TLS (Transport Layer Security). While RSA is considered less robust than Diffie-Hellman Key Exchange, Diffie-Hellman doesn't authenticate and RSA does. Both use mathematics to generate decryption keys that are all but impossible for attackers to decode, and both are used extensively today.
Diffie–Hellman Key Exchange Protocol >> It is an asymmetric cipher used by several protocols including SSL, SSH, and IPSec.
SSL/TLS uses both asymmetric and symmetric encryption to protect the confidentiality and integrity of data-in-transit.
Symmetric encryption is considered less secure than asymmetric, but it's faster and uses less computing power. To provide security over a network, these two methods are used in tandem.
SSL (Secure Sockets Layer) is an older form of TLS (Transport Layer Security), a protocol running on the application layer of the Internet that's designed to secure web communications through a TLS handshake. To establish a TLS connection, the client can either
Make a request using port 443 (reserved for encrypted HTTPS traffic), or Request that the server switch to TLS. If the server agrees, a handshake is initiated.
An asymmetric cipher generates a session-specific shared key while further communication is symmetrically encrypted. The overall connection is protected with the more secure asymmetric cipher, but beneath that, symmetric encryption is used to protect the data without slowing down transmission.
What is Hashing?
Hashing is the practice of using an algorithm to map data of any size to a fixed length. This is called a hash value (or sometimes hash code or hash sums or even a hash digest if you’re feeling fancy). Whereas encryption is a two-way function, hashing is a one-way function. While it’s technically possible to reverse-hash something, the computing power required makes it unfeasible. Hashing is one-way.
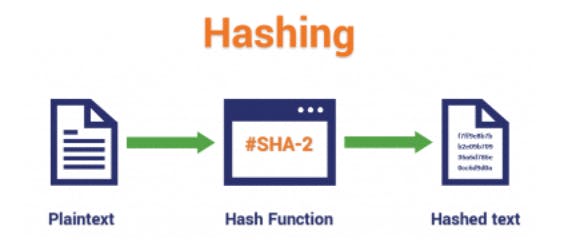
Common Hashing Algorithms are MD4 , MD5, SHA
SHA – SHA stands for Security Hashing Algorithm and it’s probably best known as the hashing algorithm used in most SSL/TLS cipher suites
Password protection with bcrypt:
Data transmitted over TLS is safe, but what about sensitive data like user passwords stored in a database?
In general, employing a robust, time-tested method like bcrypt to hash and salt passwords is great practice.
Hashing scrambles data mathematically, making reverse engineering harder.
However, hashed passwords may still be vulnerable to brute-force assaults because they are short and predictable.
Salting helps address both of these by adding a unique value to the end of a password before hashing. This makes it longer and increases entropy(randomness). Bcrypt, which has been around for decades, hashes and salts passwords in a way that slows down brute force attacks even as computing power increases. Even though it's old by some standards, it's considered industry-grade and plenty of popular authentication & authorization platforms depend on it to protect passwords.
Good Reads >> The difference between Encryption, Hashing and Salting
Encryption "In Transit" and "At Rest":
Generally, we should encrypt both in transit and at rest. Encrypting in transit these days mainly means using HTTPS rather than HTTP, making use of TLS protocols above.

Encrypting at rest means protecting data in storage. Most modern databases allow for encryption, often AES 256-bit. The best practice for password protection is to both hash and salt passwords using something like bcrypt.
Depending on your application, you may also want to encrypt while processing (for example, if you're working in fintech[Financial technology].) Cloud architecture offers great options.
Finally, modern messaging apps like Whatsapp, and Signal often use end-to-end encryption (E2EE). In these, the message is actually encrypted from one user to another, so the unencrypted message is never stored anywhere except on the user's device.
Good Reads: AWS Services
AWS KMS- Key Management Service
Happy Learning :)
